Science
SocGholish Malware Turns Software Updates into Ransomware Threats

A significant cybersecurity threat known as SocGholish is exploiting ordinary software updates to ensnare victims globally, according to new research from Trustwave SpiderLabs, a subsidiary of LevelBlue. This multifaceted threat, often referred to as FakeUpdates, operates as a sophisticated Malware-as-a-Service (MaaS) platform, allowing affiliates to distribute powerful malware, including ransomware, and extract sensitive data from organizations worldwide.
SocGholish has reportedly been active since 2017, with operations attributed to a threat group identified as TA569. Their attack strategy relies on a straightforward yet effective method: tricking users into downloading malicious files disguised as legitimate software updates, such as those for web browsers or Flash Player.
Compromised Websites and Initial Access
To initiate attacks, TA569 compromises legitimate websites by injecting malicious scripts, frequently targeting vulnerable WordPress sites through weaknesses like compromised “wp-admin” accounts. The group utilizes a technique known as Domain Shadowing, where they covertly create malicious subdomains on trusted websites, effectively bypassing security checks.
Research indicates that TA569 functions as an Initial Access Broker (IAB), offering access to SocGholish infection methods for a fee to other criminal organizations. This business model is primarily financially driven, enabling other groups to profit from attacks. Among the prominent users of SocGholish is Evil Corp, a Russian cybercrime organization with alleged links to Russian intelligence services.
Recent activities have highlighted the platform’s dangerous capabilities. In early 2025, Trustwave researchers noted that SocGholish was employed to distribute the active RansomHub ransomware, resulting in significant attacks within the healthcare sector. One notable incident involved RansomHub using SocGholish to promote malicious Google Ads that impersonated Kaiser Permanente’s HR portal, which led to subsequent attacks on Change Healthcare and Rite Aid.
State-Sponsored Links and Targeting Techniques
The research also uncovered links to state-sponsored activities, particularly connections to the Russian government through its military intelligence agency, GRU Unit 29155. The Raspberry Robin worm, a payload associated with SocGholish, has been observed in these operations, indicating the malware’s extensive reach and its transformation of trusted web infrastructure into a vehicle for infections.
The operators of SocGholish employ Traffic Distribution Systems (TDS) such as Keitaro and Parrot TDS to filter potential victims based on various criteria, including location and system settings. This targeted approach ensures that only specific individuals are exposed to the malware’s payloads. Once a system is compromised, the malware can deploy various follow-on threats, including multiple ransomware families like LockBit and RansomHub, as well as Remote Access Trojans (RATs) such as AsyncRAT and various data-stealing applications.
The findings underscore SocGholish’s adaptability and its capacity to convert legitimate websites into extensive malware distribution platforms, enhancing its status as a critical threat to organizations globally. As cybersecurity professionals continue to combat this evolving threat, the implications for businesses and individuals alike are increasingly concerning.
-

 Business1 week ago
Business1 week agoIconic Sand Dollar Social Club Listed for $3 Million in Folly Beach
-

 Health1 week ago
Health1 week agoPeptilogics Secures $78 Million to Combat Prosthetic Joint Infections
-

 Politics1 week ago
Politics1 week agoAfghan Refugee Detained by ICE After Asylum Hearing in New York
-

 Science1 week ago
Science1 week agoResearchers Achieve Fastest Genome Sequencing in Under Four Hours
-

 Lifestyle1 week ago
Lifestyle1 week agoJump for Good: San Clemente Pier Fundraiser Allows Legal Leaps
-

 Health1 week ago
Health1 week agoResearcher Uncovers Zika Virus Pathway to Placenta Using Nanotubes
-

 World1 week ago
World1 week agoUS Passport Ranks Drop Out of Top 10 for First Time Ever
-

 World1 week ago
World1 week agoRegional Pilots’ Salaries Surge to Six Figures in 2025
-

 Entertainment1 week ago
Entertainment1 week agoJennifer Lopez Addresses A-Rod Split in Candid Interview
-
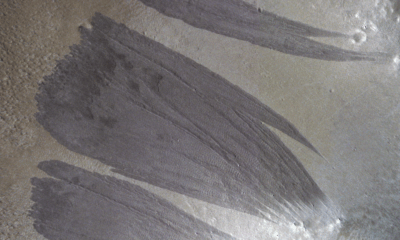
 Science1 week ago
Science1 week agoMars Observed: Detailed Imaging Reveals Dust Avalanche Dynamics
-

 Top Stories6 days ago
Top Stories6 days agoChicago Symphony Orchestra Dazzles with Berlioz Under Mäkelä
-

 World1 week ago
World1 week agoObama Foundation Highlights Challenges in Hungary and Poland