Top Stories
Urgent: New ‘Landfall’ Spyware Targets Samsung Galaxy Phones

URGENT UPDATE: A sophisticated Android spyware known as “Landfall” has been confirmed to have targeted **Samsung Galaxy phones** in a year-long hacking campaign. **Palo Alto Networks’ Unit 42** reported that the spyware first emerged in **July 2024**, exploiting a **zero-day vulnerability** in Galaxy software that **Samsung** was unaware of at the time.
The **security flaw**, tracked as **CVE-2025-21042**, could be activated by sending a specially crafted image via messaging apps, potentially allowing attackers to breach devices without any user interaction. Although **Samsung** issued a patch for this vulnerability in **April 2025**, details surrounding the malicious campaign have just surfaced, raising urgent concerns among users.
Unit 42 has noted that the spyware primarily targeted individuals in the **Middle East**, suggesting a focus on espionage rather than widespread malware distribution. **Itay Cohen**, a senior principal researcher at Unit 42, emphasized that this was a “precision attack” aimed at specific individuals, hinting at potential political motivations behind the hacking.
The investigation revealed a connection between Landfall and **Stealth Falcon**, a known surveillance vendor implicated in past attacks against **Emirati journalists**, activists, and dissidents since **2012**. However, researchers caution that the evidence does not definitively link the spyware to a particular government.
Throughout **2024** and early **2025**, samples of the Landfall spyware were uploaded to **VirusTotal** from users in **Morocco**, **Iran**, **Iraq**, and **Turkey**, adding to the urgency of the situation. The **USOM**, Turkey’s national cyber readiness team, flagged one of the associated IP addresses as malicious, supporting the theory that Turkish individuals may have been specifically targeted.
The capabilities of the Landfall spyware are alarming. It can surveil devices comprehensively—accessing photos, messages, contacts, and call logs, while also tapping into microphones and tracking precise locations. The source code analyzed by Unit 42 indicated that five Galaxy phone models, including the **Galaxy S22**, **S23**, **S24**, and select Z models, were explicitly targeted.
Unit 42 warns that the vulnerability may also affect other Galaxy devices running **Android versions 13 through 15**, escalating the risk for a larger user base. As of now, **Samsung** has not responded to requests for comments on this critical issue.
WHAT’S NEXT: Users of affected Samsung devices are urged to install any available updates immediately and remain vigilant against suspicious communications. The situation is developing rapidly, and further disclosures about the spyware and its origins are expected. Stay tuned for updates as more information becomes available.
This revelation underscores the persistent threats posed by sophisticated spyware, emphasizing the need for robust security measures in our increasingly connected world.
-
 Science3 weeks ago
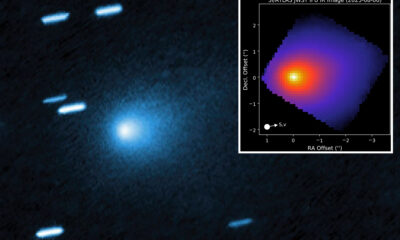
Science3 weeks agoInterstellar Object 3I/ATLAS Emits Unique Metal Alloy, Says Scientist
-

 Politics3 weeks ago
Politics3 weeks agoAfghan Refugee Detained by ICE After Asylum Hearing in New York
-

 Science3 weeks ago
Science3 weeks agoResearchers Achieve Fastest Genome Sequencing in Under Four Hours
-

 Business3 weeks ago
Business3 weeks agoIconic Sand Dollar Social Club Listed for $3 Million in Folly Beach
-

 Health3 weeks ago
Health3 weeks agoPeptilogics Secures $78 Million to Combat Prosthetic Joint Infections
-

 Lifestyle3 weeks ago
Lifestyle3 weeks agoJump for Good: San Clemente Pier Fundraiser Allows Legal Leaps
-
 Science3 weeks ago
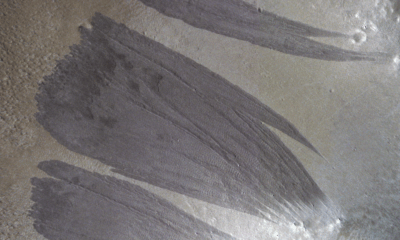
Science3 weeks agoMars Observed: Detailed Imaging Reveals Dust Avalanche Dynamics
-

 Health3 weeks ago
Health3 weeks agoResearcher Uncovers Zika Virus Pathway to Placenta Using Nanotubes
-

 World3 weeks ago
World3 weeks agoUS Passport Ranks Drop Out of Top 10 for First Time Ever
-

 Entertainment3 weeks ago
Entertainment3 weeks agoJennifer Lopez Addresses A-Rod Split in Candid Interview
-

 Business3 weeks ago
Business3 weeks agoSan Jose High-Rise Faces Foreclosure Over $182.5 Million Loan
-

 Top Stories3 weeks ago
Top Stories3 weeks agoChicago Symphony Orchestra Dazzles with Berlioz Under Mäkelä